Private hosting (Chrome)
Deploy the Applet Runner extension via Group Policy (Windows).
If your organisation requires you to use our extension on multiple devices, we have amazing news for you! Our Applet Runner extension is available for private hosting and deployment via Group Policies. This way, you can deploy our extension for multiple users under your organisation simultaneously and administrate it from a single place. This page will take you step by step on how to do this.
Requirements:
- The appropriate IT permissions at your organisation.
- The Applet Runner extension CRX file.
The CRX File and DownloadURL
The CRX file is a compressed format for extensions of browsers belonging to the Chromium family (such as Google Chrome and Edge). To obtain the CRX file of the Applet Runner extension for self-hosting, you will need to contact us and we will be happy to provide it for you.
Host the extension CRX file in an appropriate location in your IT infrastructure and create a download URL to access it. You will need this URL later in the tutorial.
About DownloadURLYou can also use the WebStore’s DownloadURL, but you won’t be self-hosting the extension and it will be retrieved from the WebStore for all your users. This is a limitation for IT infrastructures where the organisation devices do not have connection permissions to the wider internet. For this reason we recommend the self-hosting method.
The extension ID
The extension ID is a unique identifier used by the Chrome WebStore. You can retrieve it from the extension Chrome Web Store URL (last 32 characters):
https://chromewebstore.google.com/detail/cheerpj-applet-runner/bbmolahhldcbngedljfadjlognfaaeinThe extension ID of the official Chrome WebStore version is:
bbmolahhldcbngedljfadjlognfaaeinOr if you use a custom extension build, navigate to chrome://extensions/ in Chrome, and retrieve it from there. You will first need to enable Developer mode at the top right of the page in order to view the ID.
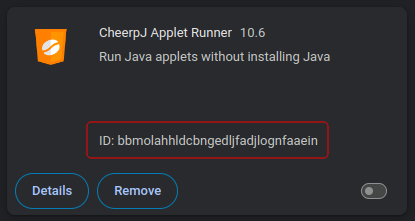
Example Extension IDCustom Extension builds all have unique IDs. The version you will be installing will have a different ID than seen on the screenshot.
You can find more information on how to pack and manually install the Applet Runner extension in our documentation.
The policy string
Now that you have the extension’s CRX file and ID, you can build the policy string by merging the extension’s ID and the CRX DownloadURL separated by a semicolon:
ID;DownloadURL
It must look something like this:
bbmolahhldcbngedljfadjlognfaaein;https://some.download.url.file.crx
Hypothetical URLThe example above contains hypothetical URL, please do not use this policy string.
Policy templates
You will need to download and install the Google administrative templates. You can do this by downloading the templates file and following the steps as stated in the Chrome policies guide by Google.
Chrome policiesCreating a new group policy
Now you have everything you need to create a new GPO, you can follow these final steps to create a Group Policy or you can edit an existing one:
- Open the Group Policy Management interface
- Go to your desired domain and right click to display the options menu.
- Click on Create a GPO in this domain, and Link it here…
- Name your policy object and hit Ok.
- Right click on top of the policy object you just created and click Edit.
- On the left menu, find the folder Administrative Templates: Policy definitions > Google > Google Chrome > Extensions.
- On the right side of the window, click on Configure the list of force-installed apps and extensions. This will display a new window with the same title.
- Click in the radio button Enabled and then click on the button Show…, this will prompt a small window named Show Contents.
- Now copy the policy string
ID;DownloadURLyou created in the previous step and paste it under the cell Value, click Ok and apply the changes.
Group policy settings
This step is optional and allows you to define additional settings for the Applet Runner Group Policy.
- Open the Group Policy Management interface, find the Applet Runner group policy you created previously and click Edit.
- On the left menu, find Administrative Templates: Policy definitions > Google > Google Chrome > Extensions.
- On the right side menu click on Configure Extension management settings.
In this window you can configure all the settings relevant for your organisation when using the Applet Runner extension. To do so you need to input the relevant settings in JSON format into the editor. This is done by editing the JSON string shown in the interface using the format:
{ "*": { "FieldKey": "FieldValue" } }The Key (*) will apply the settings to all extensions or apps under this policy. Remember to use the extension ID for those settings that you want to apply only for the Applet Runner extension.
{ "ExtensionIDHere": { "Setting1": "Value1", "Setting2": "Value2" } }You can find all the chrome specific Group policy settings in the official Chrome Documentation.
Next we will show you some examples of settings that you can configure to further enhance the user experience when using the Applet Runner extension. For example, you can enable the extension on specific URLs by default.
Enable the extension for certain URLs
If you want the Applet Runner extension to be enabled by default on certain URLs, you can use the "runtime_allowed_hosts" setting to achieve this. This way, users won’t need to click the extension icon anymore to enable it.
{ "ExtensionIDHere": { "runtime_allowed_hosts": ["*://an.example.com"] } }Pin the extension to the toolbar by default
With this setting, users won’t need to manually pin the extension anymore.
{ "ExtensionIDHere": { "toolbar_pin": "force_pinned" } }Pre-allow specific permissions
This can be useful to allow additional permissions, for example to perform downloads:
{ "ExtensionIDHere": { "allowed_permissions": ["downloads"] } }You can find more information about permissions in the official chrome documentation.
Applet Runner specific settings
These Group Policy settings are specific to the Applet Runner extension and do not originate from Chrome itself. They allow you to further configure and customize the behavior of the Applet Runner extension.
Configure clipboard behaviour
"clipboardMode" : "permission" | "system" | "java"This option allows you to configure how the clipboard will behave. Supported clipboard modes are [java], [system] and [permission]. You can find more information about the clipboard modes in our CheerpJ documentation.
Example:
{ "ExtensionIDHere": { "clipboardMode": "permission" } }Enable input methods
"enableInputMethods": booleanWhen this option is set to true the Applet Runner extension will be able to receive text input from the input method framework of the platform. This is useful to support text input for languages such as Chinese, Japanese and Korean.
Example:
{ "ExtensionIDHere": { "enableInputMethods": true } }Override browser keyboard shortcuts
"overrideAllShortcuts": booleanSome applications need to internally handle keyboard shortcuts which are also used by the browser, for example Ctrl+F. Most users expect the standard browser behavior for these shortcuts but the Applet Runner extension does not override them by default. Setting this option to true will override all browser specific keyboard shortcuts.
Example:
{ "ExtensionIDHere": { "overrideAllShortcuts": true } }Set the license key
"licenseKey": stringThis option is for paying enterprise users of the CheerpJ Applet Runner extension to remove the license text seen at the bottom of the Applet loading screen and enable full support of CheerpJ.
Example:
{ "ExtensionIDHere": { "licenseKey": "exampleLicenseString" } }Set the Tailscale Control Url
"tailscaleControlUrl": stringThis option expects a string URL of the Tailscale control plane. The control plane verifies the user’s identity and validates various keys among the connected peers in the network. Only pass this option if you are self-hosting Tailscale, if omitted, it will point to the Tailscale control plane.
Example:
{ "ExtensionIDHere": { "tailscaleControlUrl": "https://my.url.com/" } }Set Tailscale authentication key
"tailscaleAuthKey": stringThis option expects a string that contains a Tailscale auth key. Using auth keys allows one to register new users/devices that are pre-authenticated. You can create an auth key here.
InfoA combination of a user and a device connected to a Tailscale network is called a “node” in Tailscale terminology.
For more information about auth keys visit the Tailscale auth keys documentation.
Example:
{ "ExtensionIDHere": { "tailscaleAuthKey": "AuthKeyStringGoesHere" } }Update your changes
Once you are happy with your group policy configuration, you can apply these changes to see them reflected on your user’s chrome clients by running the shell command:
gpupdateNow your users should be able to see the extension installed in their Chrome browser.